Home / Technology / Notepad's New Vulnerability: Code Execution Risk
Notepad's New Vulnerability: Code Execution Risk
11 Feb
Summary
- Notepad's Markdown support enables remote code execution risks.
- Vulnerability allows external programs to run without user consent.
- Microsoft has no current solution for this high-severity issue.
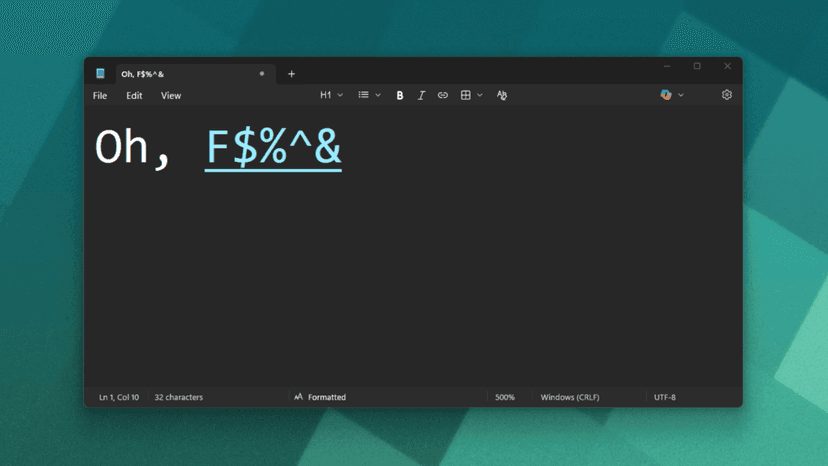
A newly discovered security vulnerability in Microsoft Notepad enables remote code execution (RCE), a significant risk for the basic text editing application. This issue stems from Notepad's recently added support for Markdown, a text formatting system. The vulnerability was highlighted by Microsoft itself in a security bulletin released on February 11, 2026.
When a user opens a downloaded file containing specially crafted Markdown text, a link can be presented that, instead of leading to a website, initiates a remote code download. This malicious code can then execute with the same permissions as the logged-in Windows user. The vulnerability carries a high CVSS score of 8.8/7.7, and Microsoft currently has no patch or solution available.
While the attack requires user interaction and the download of a separate file, it presents a serious security concern. Microsoft's current advice to users is to avoid downloading files from untrusted sources to mitigate the risk. This vulnerability did not exist in previous versions of Notepad.