Home / Technology / Fake BSOD Attacks: Hospitality Industry Targeted
Fake BSOD Attacks: Hospitality Industry Targeted
7 Jan
Summary
- Cybercriminals exploit the Windows Blue Screen of Death to deploy malware.
- A campaign targets the hotel and hospitality sector with a RAT.
- Attackers use fake CAPTCHAs and malicious scripts to gain access.
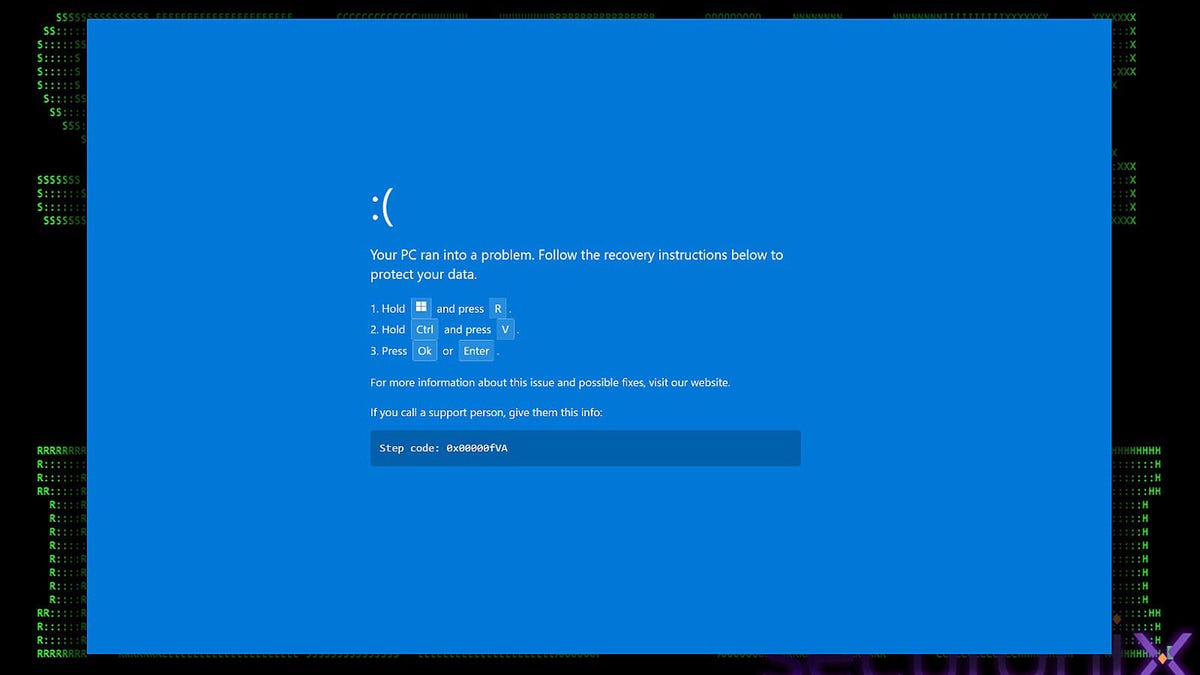
Cybercriminals are now weaponizing the familiar Windows Blue Screen of Death (BSOD) to distribute malware through a sophisticated campaign targeting the hospitality industry. This multi-stage attack chain, tracked as PHALT#BLYX, begins with phishing emails directing recipients to a fake Booking.com page. After presenting a deceptive CAPTCHA, a simulated BSOD appears, prompting users to "fix" it by executing malicious code.
The core of the attack involves a 'ClickFix' tactic, persuading victims to copy and paste a PowerShell command. This command downloads an MSBuild project file that disables Windows Defender and establishes persistence. The ultimate payload is an obfuscated version of DCRat, a potent remote access trojan capable of keylogging and deploying further malicious software.
This campaign strategically launched during the hotel industry's busy holiday season and leverages the popularity of Booking.com. Evidence, including Russian language in a project file and euro-denominated charges in phishing emails, points towards Russian threat actors targeting businesses in Europe. While average home users are less likely to be affected, organizations in the hospitality sector must remain vigilant.




